Kalwabed Rizki, Dec 30, 2020 — 6 min read
Hacker
Table of Contents
Introduction
We often hear that hackers may think, “oh, he’s the one who messes with people’s social media”, or, “he’s the one whose hobby is getting into the system and taking the data in it”, and so on.
In fact, it is true, because what we often hear is probably a crime committed by someone who calls himself a hacker. This action is usually classified as a black hat hacker.
We already know quite a bit about ‘black hat’ hackers. Maybe there will be questions like, “If there are black hat hackers, then there are white hat hackers against them?” The answer is yes, and that will be the topic of discussion this time.
What Is A Hacker
Talking about hackers, so what are hackers? referring to Wikipedia, a hacker is a computer expert who uses his technical knowledge to achieve a goal or overcome a problem, in a computerized system in a non-standard way.
In practice, hacking can use any means; it doesn’t matter whether it’s legal or illegal. Hackers, in this ‘white hat’ group, prefer to use legal (but non-standard) means to get into the target system without destroying the system until down, retrieving unauthorized data, etc. This technique is called ethical-hacking.
So it can be an analogy like: A stranger comes to the house, then someone wants to enter the house. Because the front door is locked, the person’s job is to enter without taking action that could harm the home owner. So the person tried to find out the combination of the locks on the door, and after a few tries the door was finally successfully opened and the person, because of the ‘white hat’, just left a ‘message’ to the owner of the house and told him that he got in and how to solve it. After that, he closed the door and locked it again, leaving the house without the owner’s property with him.
To know more clearly how a hacker’s step-by-step process works, there is a competition called Capture The Flag.
Capture the flag
Capture The Flag (CTF) is a special type of information security competition (from: https://ctftime.org/ctf-wtf). The point is that we are asked to find and collect a special writing format, commonly called a flag, to add points and win in this competition.
In this competition the participants are divided into teams of 1-3 people. In other cases it could be more. The material tested can also be various, usually: cryptography, stego, binary analysis, reverse engineering, web security, etc.
To find the flag we are required to solve a problem, ranging from easy to complex, which has been prepared in advance by the jury. Flag will generally be encountered in a format like: the_flag {eas_Y_t0Find_m3_8922}.
Now that we know what Capture the flag is, let’s give it a try now.
Introduction to CTF
I assume you are using a pc / laptop in this process. If not, then please listen to it and save it for later.
Okay, please open inspect element, then search for flag by (still in element inspection) Ctrl + F, then type the keyword my_flag, if true it will be found, and that’s your first flag.
What’s next? Just leave it, or Flag can be submitted in the comments column below, or it’s up to you to put it where.
Next there is an encrypted string with base64 bXlfZmxhZ3toZXJlX3RoM19zM0Nvbl9kX2ZsQV85XzFzSmkyfQ==. The flag keyword is: there is something called base64 decode.
If you can already figure out the contents, then that is your second flag. Great.
That is it? very easy, huh. Eitss in practice is much more complicated. We still come to the introductory part, not the ‘real’ one, which is more challenging.
Advanced CTF
We’re going to get into a slightly more complicated problem which we will solve together.
Please visit https://2019shell1.picoctf.com/problem/12284.
When you visit that page, do you think something is strange?
Please enter with your username & password up to you. Once logged in we will be presented with the home page:
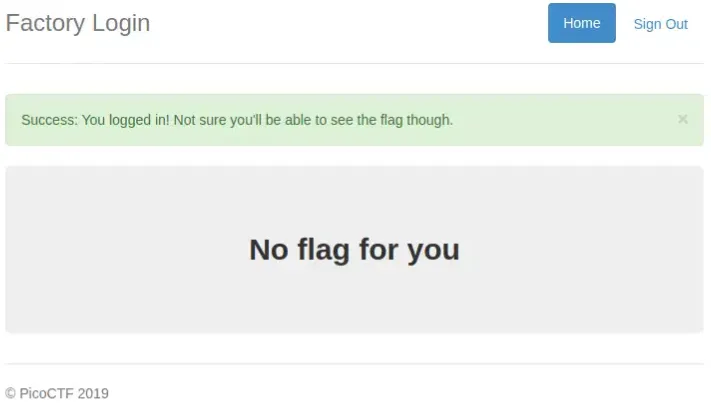
Do you feel something strange now? If so, maybe questions will arise in our minds, “how do you get in?” From here we have to start to be suspicious of the question maker. Successfully logged in but how come there’s no flag for us? Let’s explore together the source of the problem.
First, we have to make sure there is no ‘mystery box’ that we have to solve first on the start page.
Second, pay attention to the behavior of the page when it is successfully logged in without any input validation, warning, or anything else from the browser.
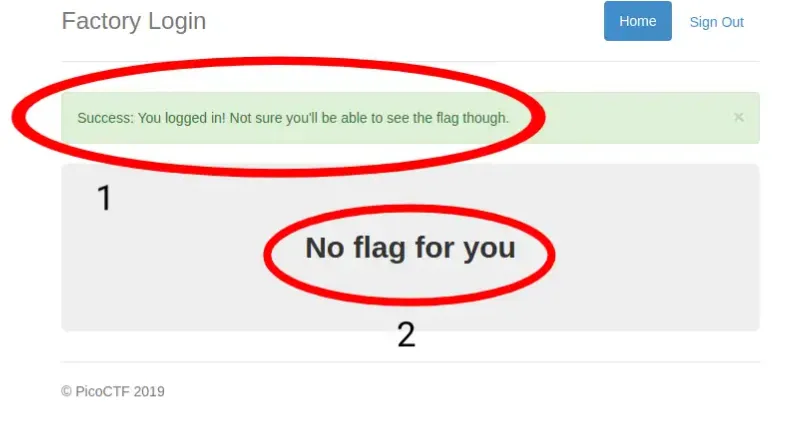
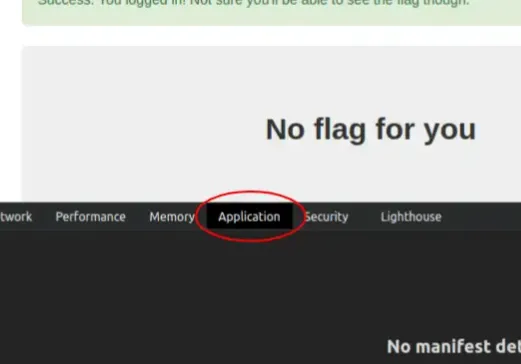
In circle number 1 we are told that we did it successfully and flag is actually already here but not visible to us.
In circle number 2 the question maker seems to signal to us that the flag we are looking for is not on this page, not at the moment. We are asked to manipulate something to bring up the flag, and that we may have realized when we saw the two interrelated circles. Indirectly, the question maker invites us to identify the content of the current page.
So what we first explored were the elements in HTML.
Is there something strange? Did the creator leave a message or something? Hm … I don’t think it’s odd.
The next step, we will check browser cookie, to see if the question maker left clue or whatever helps.
In the application, open the Cookies section, and click the url address that is there.
Look at the picture below
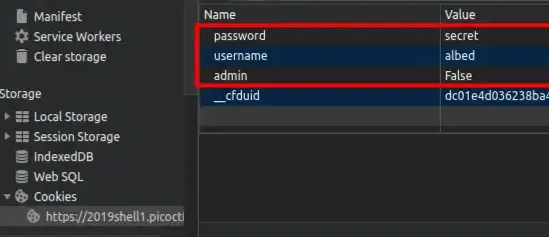
Bright dots began to appear. The question creator has given us clue to get the flag we are looking for.
Are you aware or not the username and password that we entered was in there (username & password)? Then we are also ‘told’ by the creator that we are not admins, correct? So if we are not admin and the flag is here then we need admin access to make the flag appear. So the easiest way to allow us to have admin access is to change the value of the admin which was previously False to true True.
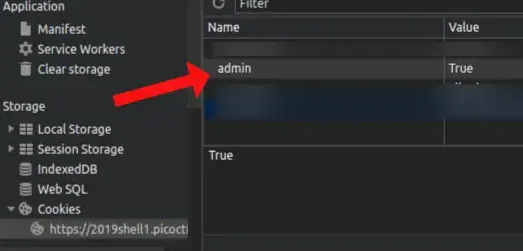
“Already changed the page, how come it still shows the same?” Because we change it in the client section then we have to notify server if we have changed the value of admin and let server process requests us by refreshing the page.
By refreshing the page, client will send Cookies to server, then the server will read us as admin (because we changed the value from admin) and if successful then the server will send the flag we are looking for to client, and client will display it to us .
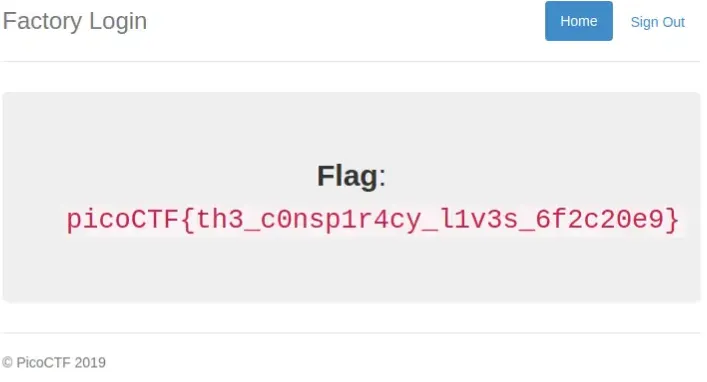
The result:
Conclusion
Now that we know a little of how those hackers work, and how we position ourselves as ‘hackers’ with a little bit of CTF play we just finished together. Hopefully this will provide us with new insights that can help us get to know and be more careful with hacking, and how feel becomes a hacker via CTF.
To beat a hacker you have to think like one.
If you are interested in practicing or learning CTF, like the example we completed above, you can visit https://2019game.picoctf.com, or https://www.geeksforgeeks.org/top-10-cyber-hacking-competitions-capture-the-flag-ctf/.
Thanks.